So my favorite script kiddy and copycat, Feross (copied, note the shameless “I discovered” in his Quora post, LoL)
Found a social engineering flaw in the HTML5 fullscreen mode that can be used for phishing attacks. This time it might be even his own finding… what do you know 😉
This flaw is very much similar to the well known and very old picture-in-picture

More info..
IMHO the old version is still way more dangers for phishing.
So How Flash is more secure?
What enables this HTML5 fullscreen flaw to exist in his prime is the fact you have full keyboard access. This way an attacker can more easily steal the user’s credentials.
After all fullscreen was existant in Flash for many years now, yet it was never compromised this way. The main reason is that Flash is more secure is that it does not allow full keyboard interaction in fullscreen.
Good thinking Adobe, taking care our security… oh wait… Flash was added with this feature with version 11.3… after all Flash can’t be left behind…
Working demo…
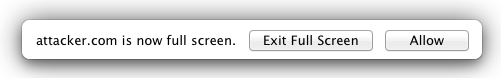
Damn… but still Flash gives you a decent popup confirmation which HTML5 doesn’t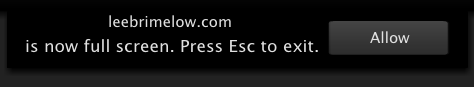
Yeah, I know Chrome give you a popup too, but *you don’t have to click on it to get FULL keyboard access.
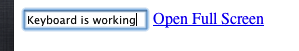
*I constructed this “amazing” demo here (chrome only), as you can see you get the message but the keyboard is fully functional and accessible through javascript.
So still Flash is more secure than HTML5 – in that respect.
It takes us back to what me and other were preaching about, that with great power comes great responsibility.
HTML5 have its own flaws and the more powerful it’ll become it will get even more.
Stay tuned…